The client believes that improving achievement is critical and essential to California’s future and that college success should be an option for every student. The client is working to remove systemic and institutional barriers to college success by enabling students to access the knowledge, financial aid, and other resources they need to earn a college degree and choose their own future.
The client is bound to keep all Personally Identifiable Information of all its students and stakeholders safe and protected from unauthorized access.
The client is utilizing a WEBSITE and various data systems to accomplish the goals set by the foundation.
SNCA is engaged in a Consulting Service provider (IT) relationship to provide a deeper understanding of the current IT systems developed by another vendor for the Client. The initial SOW was to provide
- Summary of the state of existing code base and data system
- Diagnostic Summary of the current Security mechanisms and Protocols
- Recommendations according to severity level from SNCA’s perspective for Security Threats
- Recommendations for optimization of existing ETL, PHP, and Web Focus code base.
This was to be accomplished by carrying out a detailed audit of the existing code base (ETL, WebFOCUS, PHP Portal) and a Vulnerability Assessment and Penetration Testing (VAPT) of the Client’s website and servers.
The audit is being conducted as separate streams concurrently to help in providing an assessment to Client.
We will be discussing the VAPT in this document and each stream will have a separate document to elaborate the findings.
The Vulnerability assessment included non-intrusive penetration testing. The penetration testing was conducted in phases that include Information Gathering, Enumeration, Vulnerability Assessment, Application security testing.
The objective of the assessment was to identify the security vulnerabilities that may potentially compromise the confidential data of the customer.
The goal of the penetration testing is to identify and provide recommendations to remediate the identified security vulnerabilities.
Vulnerability Assessment and Penetration Test was carried out on the Client network that comprises of the following IP addresses:
The following tests were executed in phases
Phase I: Port Scanning
- Identify TCP and UDP service running on target machine.
- Identify Service Unintentionally exposed.
- Virus/Trojan ports
Phase II: Vulnerability Scanning
- Check for accessible services on Intranet servers
- Check for operating system vulnerabilities
- Check for service-specific vulnerabilities
Phase III: Vulnerability Analysis/Penetration Test
- Perform test and check for false positive
- Rating the risk
What was not executed
>> No Denial of Service (DOS) attacks are used
Such attacks can cause data loss on live systems and are not run. Wherever
practicable, identification of systems known to be vulnerable to such attacks will be
made by other means.
>> No Brute-Force attacks
This is most effectively performed on-site by internal staff at regular intervals and is
not included in this service
Summary of Finding
In all 35 ports were tested within the Client System and they are classified based on a scale of risk rating from Critical to Low. Critical being the highest vulnerability of loss of data to external sources.
An explanation of the Vulnerabilities is attached as an appendix for a quick read to this Executive summary.
Risk Level Ratings
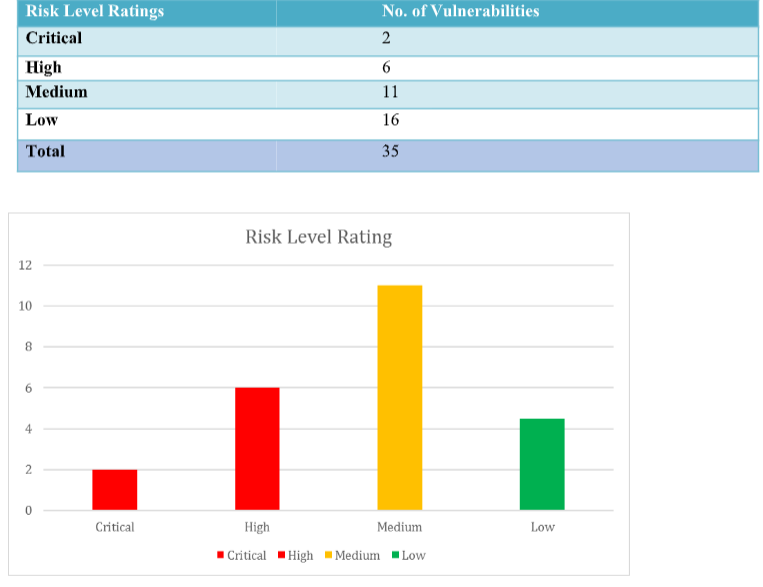
The audit unearthed both critical and high vulnerabilities that may comprise the sensitive information within the application.
Medium and low vulnerability also exist but do not possess a major threat in the current
infrastructure.
Client WEBSITE is
“Highly Vulnerable “
i.e. there exists vulnerabilities within the system that will allow an attacker to easily penetrate the system and can download the sensitive data that pertains to the users and misuse it in an unauthorized manner.
In Conclusion
The client did the right thing in ordering an AUDIT and VAPT of their existing system. This enabled the team to have a plan to fix the immediate Critical and High Vulnerabilities.
It is highly recommended that the following vulnerabilities be fixed on high priority:
- Password Policy – This is a critical High vulnerability. A strong password policy needs to be enforced, to prevent attackers to hack passwords by using sophisticated password
breaking tools. - Cross-Site Request Forgery – Attackers can make changes to a user’s profile without the user’s knowledge. Refer solution for fixing this vulnerability.
- All the High severity vulnerabilities like Application traffic, Poor session management and Session fixation should be fixed prior to releasing in production.
- Medium vulnerabilities can be fixed later.
- Low ones are good to fix, but not a severe threat.
APPENDIX A
LEGEND: VULNERABILITY LEVEL
Determined based on existence of highest level of vulnerability found within the system.
CRITICAL/HIGH: Presence of ‘Critical’ / ‘High’ Vulnerabilities.
Makes it easy for an attacker to penetrate into the system
MEDIUM: No ‘Critical’ / ‘High’ Vulnerabilities found.
Presence of one or more ‘Medium’ vulnerabilities
A skilled hacker could potentially penetrate into a security
loophole
LOW: No ‘Critical’ / ‘High’ / ‘Medium’ Vulnerabilities found.
‘Good to have’ best practices for maintainability
Critical Vulnerabilities:
- Password Policy: Users should be enforced to set a strong password to their profile which cannot be easily guessed by sophisticated password guessing tools. The change password functionality was tested for setting different passwords to the user’s profile. It was found that password as weak as a single character could be set. Enforcement of password policy is not done properly.Applications allowing such weak password is prone to password guessing attacks.
Solution: The password change functionality should validate the password to see if the password set by the user is as per the password policy. - Application traffic not encrypted: Application use http protocol. All the user input to the website is insecure and can easily read using specialized tools.
Solution: Use https protocol. HTTPS is secure http protocol. It encrypts the user input to website which means, all the input received is garbled and can only be read by the website.
High Vulnerabilities:
- Poor Session management: User practically do not logout from the website even if the sign out button is clicked. Ideally when sign out button is clicked, the user should be redirected to the login page and even if back button is clicked, the user should not be able to access the profile, unless authentication process is followed. At server end, when sign out instruction is received, the mapping of user to the session identifier should terminated/expire and cannot be reused. So when attacker reuses the session identifier to gain access to user’s profile, it redirects to login page and requires authentication process to be followed.
Solution: Application function at server that allocates unique identifier (cookie) to the users who login into website should terminate/delete the identifier once sign out instruction is received from the users. - Session Fixation: A hacker can set unique identifiers (cookie value) for a legitimate user before the user signs into the website. Thus when the user signs in the website, attacker know the unique identifier in advance and may misuse it.
Solution: The unique identifier (cookie value) before and after sign in to the website,should not be same. New identifier should be allocated after sign in. - Cross-site request forgery: Hacker can force a legitimate authenticated user to perform a function without the knowledge of user. Ex: hacker can trick user ‘A’ to change profile password without knowledge of user. Hacker can set his own password to user A’s profile making it inaccessible to the user.
Solution: Set randomly generated tokens for every important functionality perform on the website.
Medium Vulnerabilities:
- Cross Frame Scripting: The attacker induces the browser user to navigate to a web page that is controlled by attacker; the attacker’s page loads our website page in an HTML frame; and then JavaScript executing in the attacker’s page steals data from the website page
Solution: Configure application webserver in such a way that for every response provided
from the website has header “X-FRAME-OPTIONS: SAMEORIGIN”. This ensure HTML frames within the website are only loaded to the user browser and they are not controlled by attacker. - Trace and insecure HTTP methods enabled: Every Web servers has some methods used basically by application administrators to modify the application as required. Hacker can use these methods to alter the website and load illegal web pages or delete legitimate content from application.
Solution: Identifying and disabling all insecure http methods
Low Vulnerabilities:
- Poor Error and Exception handling: Sometime website tend to provide errors and exceptions due to unknown problem. Such error may reveal sensitive information related to the website. Thus allowing attacker to design their attacks.
Solution: designing generic error pages and displaying it when web application faces any unknown problem.